
Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.
So no, there's no such thing as a perfectly secure and truly private smartphone, let's get that out of the way now. But you practically need a smartphone to get by in society, so which phone at least manages to be the lesser of all the evils?
With critical vulnerabilities like the KRACK exploit and Blueborne, not to mention the FBI trying to find a backdoor into phones, that's a hard question to answer. TCL shutting down production of BlackBerry devices certainly doesn't help, either.
So to find the most security-hardened phones, we looked for key factors like encryption strength, biometrics, hardware-assisted security, VPN availability, and security patch timeframes. Our research narrowed the list down to four great phones, so let's discuss how well each of these devices protects your privacy.
Table of Contents
- Comparison Chart
- Chart Key
- Methodology
- Phone 1: Pixel 4 XL
- Phone 2: Galaxy S20 Ultra
- Phone 3: iPhone 11 Pro Max
- Phone 4: Sirin Finney
Comparison Chart
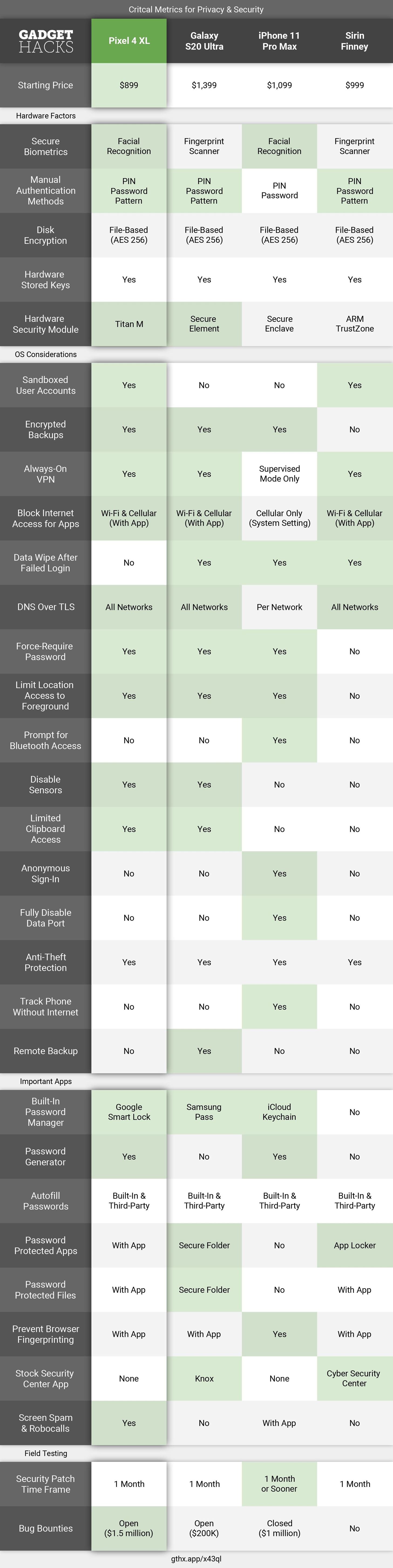
Key Comparison Points
Hardware Factors
- Secure Biometrics: Biometrics have their pros and cons. Con: If your biometric identifiers were ever stolen, you wouldn't be able to change them like a password, so they'd be permanently compromised. Pro: if a security method is easier for the user, they'll be more likely to actually use it. So in the end, it's your call as to whether biometrics are a good or bad thing, but note that we did give 3D face scanners the edge since they're harder to fool than other biometrics.
- Manual Authentication Methods: The different ways in which a user can manually unlock the lock screen and access data on the phone.
- Disk Encryption: Modern phones use one of two types of encryption: file-based (FBE) or full disk (FDE). File-based encryption is the more effective method of the two, as it allows individual files to be locked with different keys, whereas full disk encryption uses only one key to lock the entire data partition.
- Hardware-Stored Keys: Each of the phones on our list calls upon a specific hardware component to store cryptographic keys. These keys are stored in isolated parts of the processor (or on isolated chips), which are then used to unlock the device and verify each stage of the boot process.
- Hardware Security Modules: An isolated processor or separate chip where sensitive data is stored. Transactions that involve this data are conducted here to ensure maximum protection.
OS Considerations
- Sandboxed User Accounts: If privacy is one of your top considerations, you may want to maintain separate user spaces on your phone — perhaps one for work and another for your personal usage.
- Encrypted Backups: Whether your data, when backed up to the cloud, is secured with encryption. If the cloud server were hacked and someone tried to restore your data onto their phone, they'd have to know your lock screen passcode to decrypt the backup.
- Always-On VPN: A virtual private network, or VPN, allows you to reroute internet traffic through an external server. A good VPN service will even let you encrypt all data traffic for increased anonymity. With Android devices, you can funnel all types of internet traffic through a VPN. With an iPhone, however, you can only use a VPN over Wi-Fi, unless you're willing to reset your device and enable "Supervised Mode" to get the VPN working on your mobile data connection.
- Block Internet Access for Apps: If you don't want apps "phoning home," the ability to block internet access on a per-app basis is a huge plus. With Android, this can be done by setting up a local VPN like Netguard, which takes a little extra work. With iOS, you can easily disable mobile data access for an app, however, it's not possible to restrict Wi-Fi connectivity.
- Data Wipe After Failed Login: Some phones have a feature that triggers an automatic factory reset when someone attempts to enter your PIN or password too many times. This is very effective when it comes to fending off intruders, as it makes brute-force password attacks all but impossible.
- DNS over TLS: DNS is the server that finds the IP address corresponding to a specific URL (such as gadgethacks.com) and directs your phone to the site. Typically, this interaction is unencrypted, but thanks to DNS servers such as Cloudflare, this can now be a secure and private interaction using Transport Layer Security (TLS). Android 9 introduced a "Private DNS" option, which automatically switches all DNS connections (whether on Wi-Fi or cellular) to your DNS server of choice. For older versions of Android and iOS, you have to change this setting for each network connection manually.
- Force Password to Unlock Phone: The ability to quickly disable biometrics and require a PIN or password to prevent others from forcing their way into your phone using the fingerprint scanner or facial recognition.
- Limit Location Access to Foreground: When an app requests access to your location, you can limit access to only when the app is open. This protects you from apps that use this permission in the background to monitor your movements secretly and send that information to their servers (or sell it to advertisers).
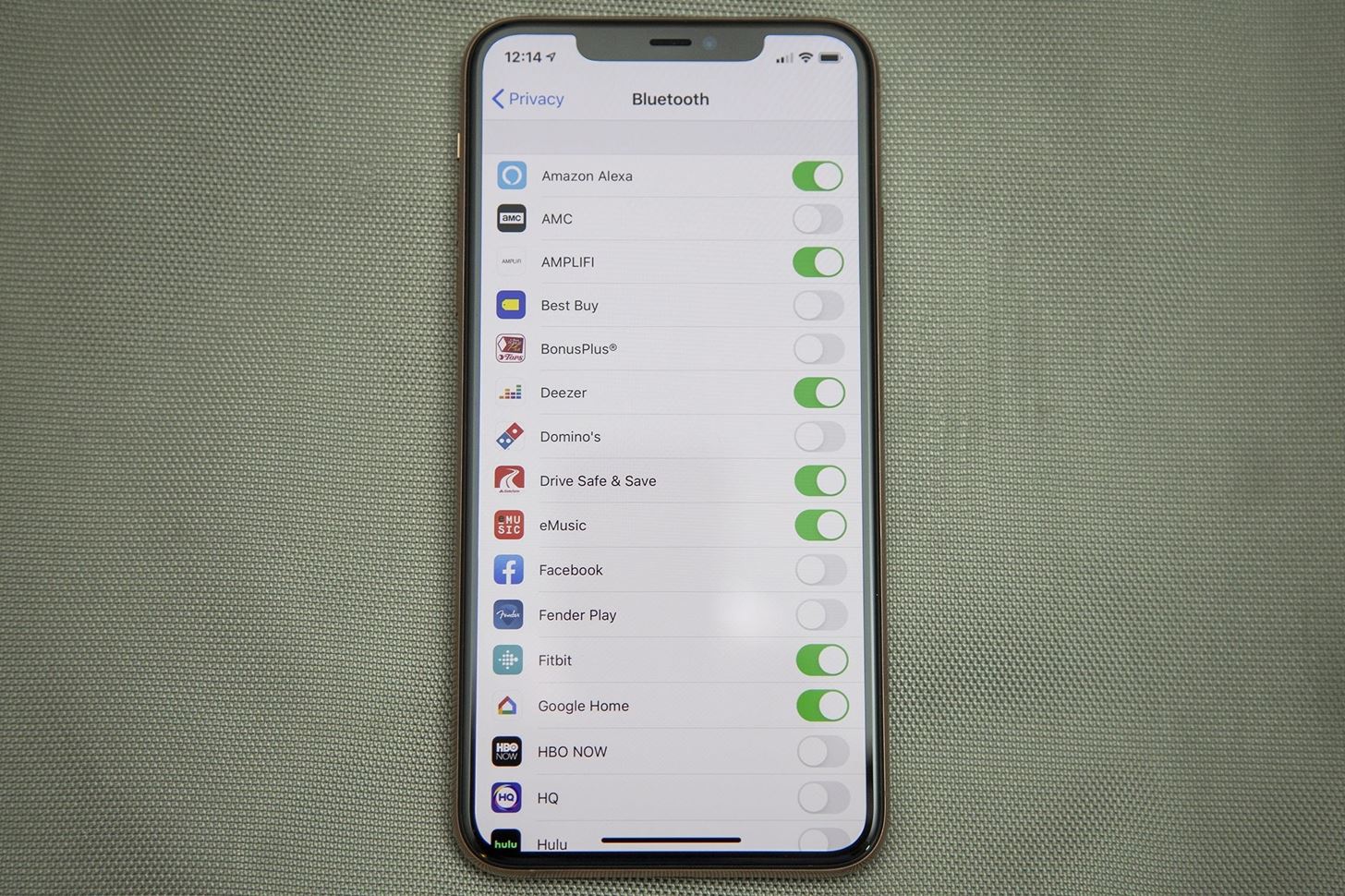
- Prompt for Bluetooth Access: When an app requests access to Bluetooth, iOS 13 requires the developers to justify the reason to the user in a prompt. This way, you know exactly how Bluetooth will be used and, based on the reason, can make the best decision for you whether to grant it or not.
- Disable Sensors: The ability to disable the many "other" sensors in your smartphone. While it is possible to turn off Wi-Fi, Bluetooth, and GPS, only with Android 10 can you disable the other sensors (such as the accelerometer, magnetometer, and microphone), many of which can be abused by hackers.
- Limited Access to Clipboard: By default, apps do not have access to your clipboard data. The clipboard is where your phone stores all text you cut or copy. Currently, only Android 10 limits this.
- Anonymous Sign-In: Instead of using your real email address to create an account for an app, you can sign in with a fake email address that forwards the emails to your real one. This protects your account from spam emails by limiting who knows your address.
- Fully Disable Data Port: Having the ability to prevent a device that connects with your phone via the data port from communicating with your phone. Known as USB Restricted Mode, this feature disables the Lightning port one hour after you last unlocked it. So far, this feature is exclusive to iOS.
- Anti-Theft Protection: Whether the device has built-in protection to prevent your phone from being stolen and your data from being accessed. There are three main features a phone's anti-theft protection must provide in order to qualify here: remote wipe, remote tracking, and remote lock.
- Track Phone in Airplane Mode: The ability to track your lost or stolen phone when location and Wi-Fi are disabled. A new feature added in iOS 13, your iPhone will periodically send an encrypted location report to nearby iOS devices via Bluetooth. This information is then relayed to your Find My iPhone account via the nearby iOS device's internet connection.
- Remote Backup: While remote wipe is great for protecting your data, it also locks you out from the data not backed up to the cloud. With remote backup, you can backup your phone first before wiping it. This way, you can retrieve your data, then remove it safely from your stolen or lost smartphone.
Important Apps
- Built-in Password Manager: The name of the included feature that stores your various login credentials. These screen names and passwords are stored in an encrypted vault, which offers the ability to autofill the stored information in the appropriate app or website.
- Password Generator: The password manager can generate a new password, which is more secure than your existing passwords.
- Autofill Passwords: The ability to autofill passwords without the use of the clipboard. Every phone on our list supports this feature with both the built-in password manager as well as third-party options.
- Password Protected Apps: Because there are times when we need to lend our phone to others, being able to lock individual apps is a huge plus. Listed is the name of the preinstalled app that allows you to lock other apps using a password or biometrics.
- Password Protected Files: Similar to apps, protecting sensitive files (such as photos and videos) is essential when more than one person can access a phone. These apps allow you to protect files as well, using a password (which is separate from your lock screen password) or biometrics.
- Prevent Browser Fingerprinting: Browser fingerprinting is a method of tracking your device by gathering uniquely identifiable information about your browsers such as the operating system of your smartphone, active plugins, timezone, screens resolution, and more. The combination of this data is used by websites to track your device across pages, getting an idea of your online activities.
- Stock Security Center App: If you're security-minded, it's good to have a centralized app that helps you handle all of your phone's security needs. For example, the DTEK security app gives you an overview of your phone's security health and allows you to tweak important security settings, among other things, easily.
- Screen Spam & Robocalls: The ability to automatically screen or block calls determined to be spam, scams, or robocalls.
Field Testing
- Security Patch Timeframe: Apple doesn't adhere to a specific timeframe with its security patches, however, updates are generally issued within a month of critical bugs being found. Android releases security patches monthly and leaves it to the OEM to distribute to their devices. Since Apple has shown to release critical security patches in under a month, the iPhone gets the win here.
- Bug Bounties: Device manufacturers will usually offer a cash prize for anyone who can find glaring weaknesses in their phone's software, effectively crowd-sourcing the process of discovering and closing security loopholes. With a higher bounty, people will generally be more motivated to find these bugs. Some companies only invite trusted bug reporters to earn a bounty (depicted as "Closed" in the above chart), while others will let anybody report bugs and claim the bounty (shown as "Open" here).
How We Chose These Phones
Our first requirement in choosing these phones was that they all had to be available for sale in the United States from a major carrier or manufacturer. Secondly, for a phone to make this list, it had to be encrypted by default to ensure that your data is protected against external access.
Another requirement was that the phones all offered granular permission management, which allows you to revoke an app's permission to access certain features like your camera and microphone. Then, to ensure that your data remains safe even when your phone is lost or stolen, we only selected phones with anti-theft protection.
But what really helped narrow down our list was keying in on additional security features.
We looked for phones that included extra security features beyond the standard OS-level stuff — for example, strengthening the hardware or adding a security center. With these features, we know these phones took a more dedicated approach to protect your security.
With that in mind, we eliminated many popular phones that too heavily relied on Android's basic built-in security features and Qualcomm's generic hardware security module. Phones such as the LG V50, LG G8 ThinQ, Moto Z3 Play, and OnePlus 7 Pro.
It's also worth noting that some of the phones that made our final cut had sibling devices that could've also been listed here — for example, Apple's iPhone 11 Pro and Samsung's Galaxy S20+ or S20. We left these devices off the list since the higher-end option was more future-proof.
After eliminating the phones which didn't meet our requirements, the finalists were ranked based on how well they scored in the key comparison points above, and with that, the following phones rose to the top.
Phone 1: Google Pixel 4 XL
Last year, our second-place phone was the Google Pixel 3 XL. It only lost to the BlackBerry Key2, a phone built for enterprise and security, but not much else. Fast forward to 2020, and TCL has stopped selling BlackBerry phones, allowing this year's Pixel 4 XL to slide into first place as the best option still standing.
Let me start by saying that when it comes to privacy and security, it doesn't matter if you get the Google Pixel 4 or 4 XL. There are no additional protections found in either variant, so opt for whichever phone best fits your hand size and budget.
At the heart of the Pixel 4 XL's security is the Titan M chip, an enterprise-grade security module based on a similar chip used to protect Google's cloud data centers. It handles all sensitive transactions such as mobile payments and apps targeting the StrongBox KeyStore API (added in Android 9), and it's physically separated from the SoC to further protect it.
The map of your face used in the new 3D face unlock feature is also stored in the Titan M. When using this method of authentication, the new face capture is compared to the stored version in the Titan M security chip, minimizing any tampering opportunity. Even the lock screen passcode is verified within the Titan M.
To ensure Titan M remains uncompromised, its firmware will never be updated unless you input your passcode. It even protects against bootloader tampering, the firmware in charge of starting up Android. Rollback protection, a feature that prevents hackers from downgrading your phone to an older (and less secure) version of Android, is also provided by the Titan M.
Google has been aggressively hardening Android's security for the last few years. One of the biggest updates came in 2018 with Android 9, which included more than 12 major changes that specifically target privacy and security. Android 10 has only expanded on this with improved location permissions and additional protections that change how apps can interact with your personal data — for example, apps can no longer read your clipboard under any circumstances.
New to the Pixel series this year is 3D face unlock. With Android 10's native support for facial recognition, you can use this technology to authenticate yourself for sensitive transactions such as payments. As with Face ID, Google's facial recognition is more secure than other biometrics thanks to the detailed mapping of your face .
You might think a phone made by Google shouldn't be considered a top pick for privacy, but none of the Pixel's extra features (beyond those included with stock Android) give Google any more access to your personal data. As with any phone or computer, if you use Google services, Google may record a history of that activity.
But security is where this phone really excels. With Google's hardware- and software-based protections, you are relatively safe on the web. You're even protected against spam calls thanks to the AI-powered Call Screen features. Thanks to three years of full OS updates, protection will only get better over the life of the phone.
Phone 2: Samsung Galaxy S20 Ultra
Samsung has a long history of catering to enterprise users. To tap into this larger market segment, they had to improve their devices' security beyond the basics provided by Android. The result was Samsung Knox, a combination of hardware and software to provide deep-level protection that starts at the SoC. And while regular consumers don't have access to many of these features, they are available for any company you join with a BYOD policy.
At the heart of the Galaxy S20 Ultra's protection is the Secure Element. Samsung has joined Apple and Google in creating their own security chip specifically designed to manage sensitive transactions and isolate private data. It is in this chip that Samsung manages Samsung Pass, Secure Folder, and many of its numerous security features.
During manufacturing, each Samsung Galaxy S20 Ultra is injected with a Device Root Key (a cryptographic key) that can only be accessed in the Secure Element. This key is unique to each device and is used, alongside the Secure Boot key, to detect any tampering with the operating system or bootloader.
It is because of these keys that it is nearly impossible to flash custom software on the Galaxy S20 Ultra (Exynos variant) without tripping the Knox Counter, a hardware-based flag that activates once you attempt to load any custom recovery or firmware. Once tripped, Knox is no longer available as the security and protection advertised by Samsung can no longer be guaranteed.
Knox also includes Samsung Defex, a patch to the kernel that prevents root from being granted to apps even after root was successful. So even if you trip the fuse and forgo access to Knox, Knox is still protecting you. Real-Time Kernel Protection tracks kernel changes and prevents the phone from booting if any tampering has been done.
Samsung is one of the few Android phones that will wipe your data upon subsequent failed login attempts. When enabled, after 15 failed attempts, the phone will automatically factory reset itself to protect your data from the intruder.
With the Galaxy S20 Ultra, you get the power of Knox to protect you each day. Its extensive protection covers you even if you manage to root the device, something few other OEMs offer. At its core is Android 10, the more secure and stable version of Android yet, that keeps you safe when using apps or browsing the web. And with Samsung's recent track record, you can expect up to date security patches for years to come.
Phone 3: Apple iPhone 11 Pro Max
I'm sure you've seen Apple's ads that focus on privacy. It is a theme that Apple has been pushing recently, and rightly so. Not only has iOS been considered the more secure platform for years, but the FBI famously couldn't crack it. With the iPhone 11 Pro Max, you have an even more secure iPhone thanks to improvements to iOS 13 and Face ID that make it challenging for anyone but yourself to access.
With iOS 13, Apple is making users more informed about their apps. Similar to Android 10, if an app accesses your location in the background, you'll get a notification with the option to deny it future access or limit location usage to only while the app is open. In prior versions, Bluetooth was accessible to apps without regard to why an app needed this permission. In iOS 13, apps must define how they plan to use Bluetooth and you're able to allow or deny access.

Find My has been a staple in iOS for years, allowing you to track your Apple devices remotely along with other anti-theft protections. New with iOS 13 is the ability to track your iPhone even when the device is offline. So if someone steals your iPhone and disables its internet connection to abscond from Find My, it sends an encrypted location report to any nearby iOS 13 devices via Bluetooth, which can then upload the report to Find My on your behalf.
But the most significant privacy addition is the "Sign in with Apple" feature. Facebook and Google have had sign-in options for years, allowing you to log into a third-party app with your corresponding account. But this typically gives the app access to some of your data on those accounts. With the new "Sign in with Apple" button, you can sign in with essentially a throwaway email address that relays messages to your real email address. So your data is safe and it's easy to ghost the service if you want to.
Now let's turn our attention to the hardware. The 11 Pro Max uses Face ID, which is still one of the best biometrics available on a smartphone. It's now 30% faster than previous versions while still retaining its stellar 1 in 1,000,000 chance of registering a false positive (unlocking your device for the wrong person).
Over 30,000 dots are projected onto your face to create a 3D depth map. This map is then encrypted and stored in the Secure Enclave, an isolated environment of the SoC. Each time you unlock your phone, a new map is made and compared to the one stored. If it is a match, it unlocks your device. And for added protection, it requires your eyes to be open , preventing someone from unlocking your phone while you are sleeping.
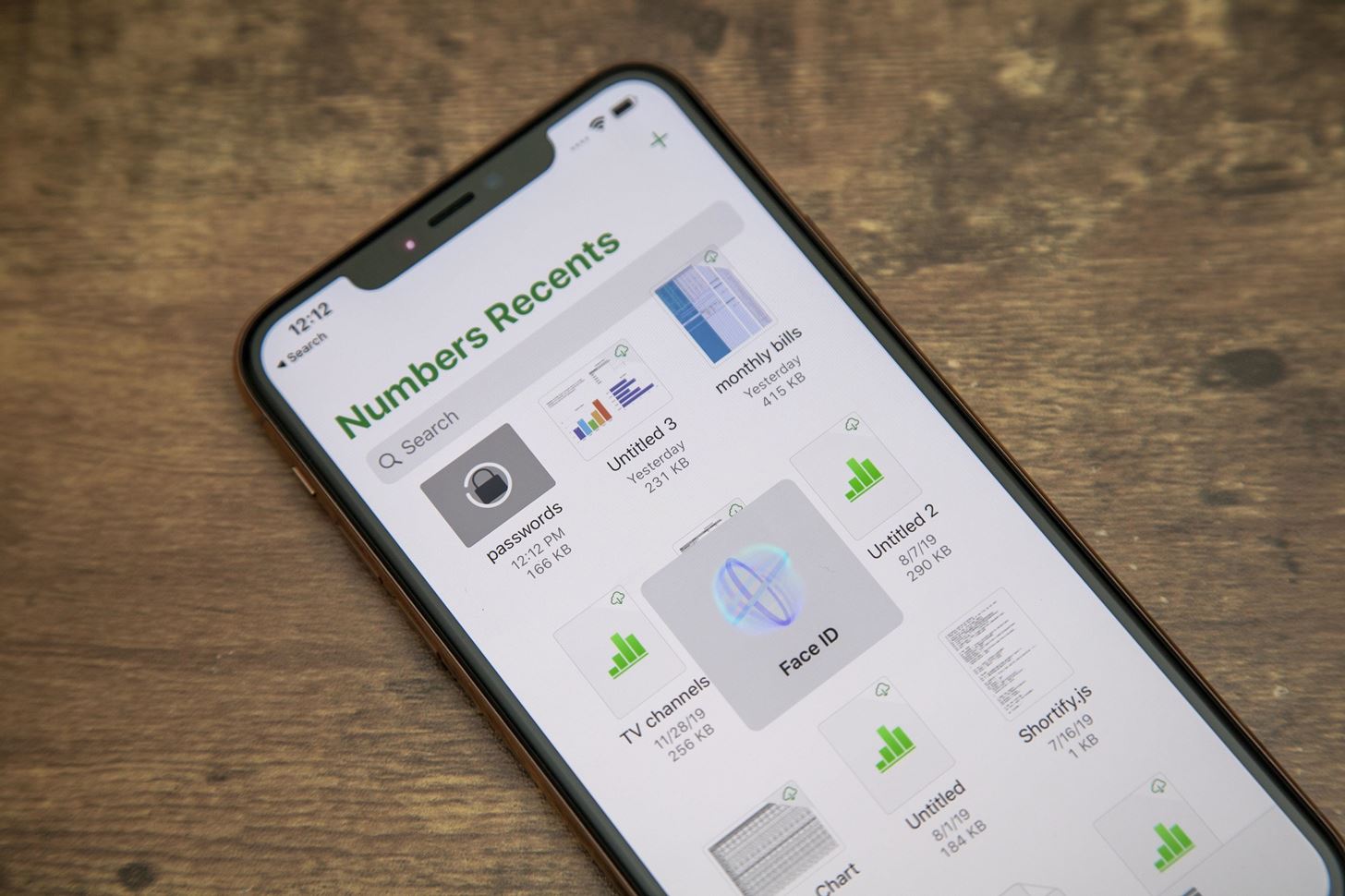
Another feature that security users will enjoy is the built-in password manager on iPhone 11 Pro Max. With iCloud Keychain, you can store all your passwords and generate new ones for the apps you use. These passwords can be autofill into apps and browsers. The passwords are encrypted with keys stored in the Secure Enclave for maximum protection.
While the iPhone 11 Pro Max's price tag isn't the most budget-friendly cost, this year, there are options that can save you money while offering the same great privacy protection. For example, the iPhone 11 is a few hundred dollars cheaper and shares all of these benefits.
Phone 4: Sirin Finney
When BTC hit an all-time high of $20,000, millions of new investors swarmed the cryptocurrency market to try to jump in on the action. Companies in all fields realized the potential of this market, and thus, phones such as the Sirin Finney came to fruition.
Its starts with Sirin OS, the proprietary Android skin created by Sirin Labs and built from the ground up to secure all possible weak links that could compromise the security of cryptocurrency transactions.
The heart of this is the BlockShield, a multi-layer protection system which provides features such as IP address hiding and MAC address randomization. Similar to other phones on our list, the Sirin Finney uses a hardware root of trust system to ensure no component has been tampered with before booting up the phone. It even includes a feature known as Trusted Display which protects all inputs (such as touches on the screen) using ARM's TrustZone so hackers can't use a keylogger.

Another significant component of the security is the Behavior-based Intrusion Prevent System. Using machine learning, the IPS is able to detect attacks from virtually every aspect of the phone. This system continues to learn your behavior, allowing it to understand the differences between an activity you conducted versus something abnormal and likely from a hacker.
The Sirin Finney comes with a number of apps to ensure all your communications are secure as well. For example, ProtonMail comes preinstalled to provide encrypted emailing, and the Koolspan Trust Call app provides encrypted voice calls.

These apps , along with several others such as Wallet, are sandbox from the rest of the OS to strengthen their security. Known as the SecureShield, this feature isolates these apps from accessing sensors and components which could, when used maliciously, compromise the security of the phone. These sensors include the camera and the microphone.
There are many more ways in which Sirin Labs protects its customers. Sirin Finney is a phone that they hope will become the go-to device for cryptocurrency. The skin, Sirin OS, provides protection on all levels, so you can securely house your alt coins and your data. While it lacks some other security features found on other devices, it is more than worthy of a spot on our list.
This article was produced during Gadget Hacks' special coverage on smartphone privacy and security. Check out the whole Privacy and Security series.
Just updated your iPhone? You'll find new Apple Intelligence capabilities, sudoku puzzles, Camera Control enhancements, volume control limits, layered Voice Memo recordings, and other useful features. Find out what's new and changed on your iPhone with the iOS 18.2 update.


















1 Comment
Is this supposed to be satire? An article about the best phones for "security and privacy"
1 of the phones is one that nobody on the planet has ever heard of and therefore has zero credibility.
2 are phones built around google services, a multi billion dollar tax avoiding amoral company that is known for collecting as much data as possible and for tracking every single thing you do with your phone
1 is a phone from apple, the only other company on the planet that is equally as morally bankrupt as google, apple is also a multi billion dollar tax avoiding cesspool.
You have listed 4 phones on the pretense of suggesting phones for privacy and security but all the phones you listed are poor quality, made in chinese sweat shop, hunks of intrusive garbage that are tied directly to apple and googles big brother data collecting servers. You could have chosen quite literally any other brand of phone currently on the market and while they may use android they still wouldnt be as infested with googles data collecting bs as the ones you listed
Share Your Thoughts