
As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.
While companies like Facebook, Snap, and Twitter do a formidable job against the waves of attacks they receive daily, they are not impenetrable. So don't just rely on them, take some time to set up your own defenses.
Use a Burner Email
Most social media apps ask for an email address when signing up. Email services are a haven for cyberattacks, and if yours is compromised, hackers can then reset your password to get full access to your account and the ability to lock you out.
You can either protect your primary email address closely, or you can just use a throwaway email address. You'll avoid all the spammy emails sent by the social media site, and if the address is ever compromised, you can just ditch it and use another with your social accounts.
While you can create a free fake email address using the major email providers such as Gmail, Yahoo, and Outlook, we recommend using the app "Temp Email." This app allows you to create an obviously fake email that can be created (and destroyed) in seconds. Check out how it works below!
Don't Share Your Real Number
Sharing your real number online is a bad idea — only do it if you're ready for robocalls, spam, or maybe even stalkers. And if they know your phone number, a hacker can begin the process of SIM-jacking, a recent exploit to take over your phone number (and, by extension, your accounts).
A great way to combat this is to use a burner number. Using an app (you can find our top picks at the link below), you create a temporary number that can be disposed of at any time. Use this number to create accounts, and update existing accounts to be associated with this number. When you don't need it, just burn it.
Lock Your Social Apps in Password-Protected Folders
Not all threats come from afar — often, our accounts are hacked by people around us. Your first line of defense against this is a strong password. But to be extra safe, you need to add layers.
A password-protected folder provides a second layer of protection by housing certain apps in a vault. Apps within the vault are accessible only with a password that can (and should) be different from your phone's lock screen code.
While there are a third-party apps like IObit to help you do this, some phones come with this feature built in, such as Samsung's Secure Folder and BlackBerry's Locker. Either way you go, the extra layer of security will go a long way towards protecting you against local threats.
Use 2-Factor Authentication (Not 2-Step Verification)
Most social media apps have two-factor authentication (2FA), which is a security protocol where you need two different factors to log in. These can be something you know, something you have, or something you are. For example, a password could be something you know, while a USB security key could be something you have.
2FA should not be mistaken for two-step verification (2SV), which also requires two factors, but unlike 2FA, can be two factors from the same category. Although two-step and two-factor are sometimes used interchangeably, they are not the same thing — true 2FA is better.
One of the best ways to add 2FA to your accounts is with the help of a 2FA app. These can serve as a software-based security key (something you have) without the vulnerabilities that come with SMS code systems. If you'd like a recommendation here, check out our full review of 2FA apps below. Otherwise, you can learn how to set up 2FA on your accounts.


Get a Good Password Manager
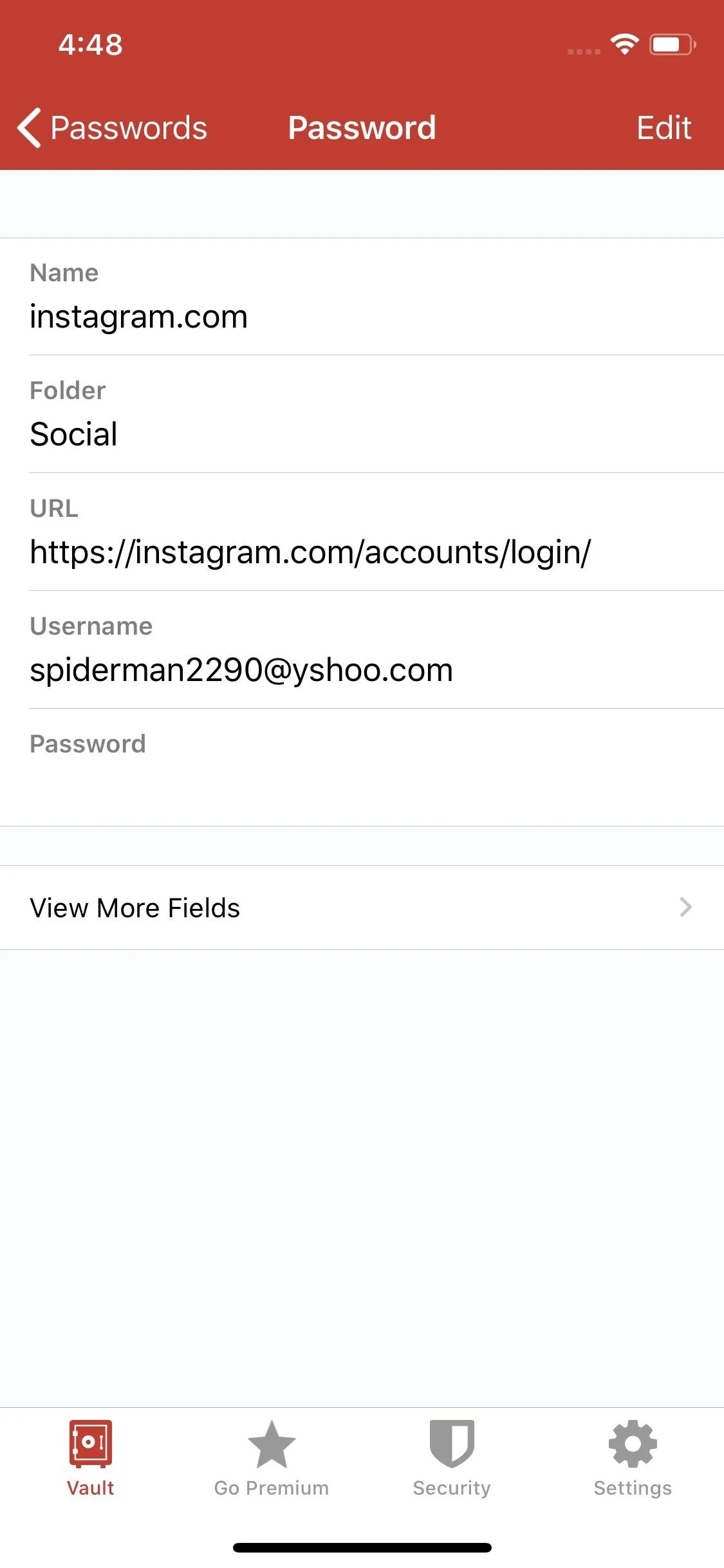
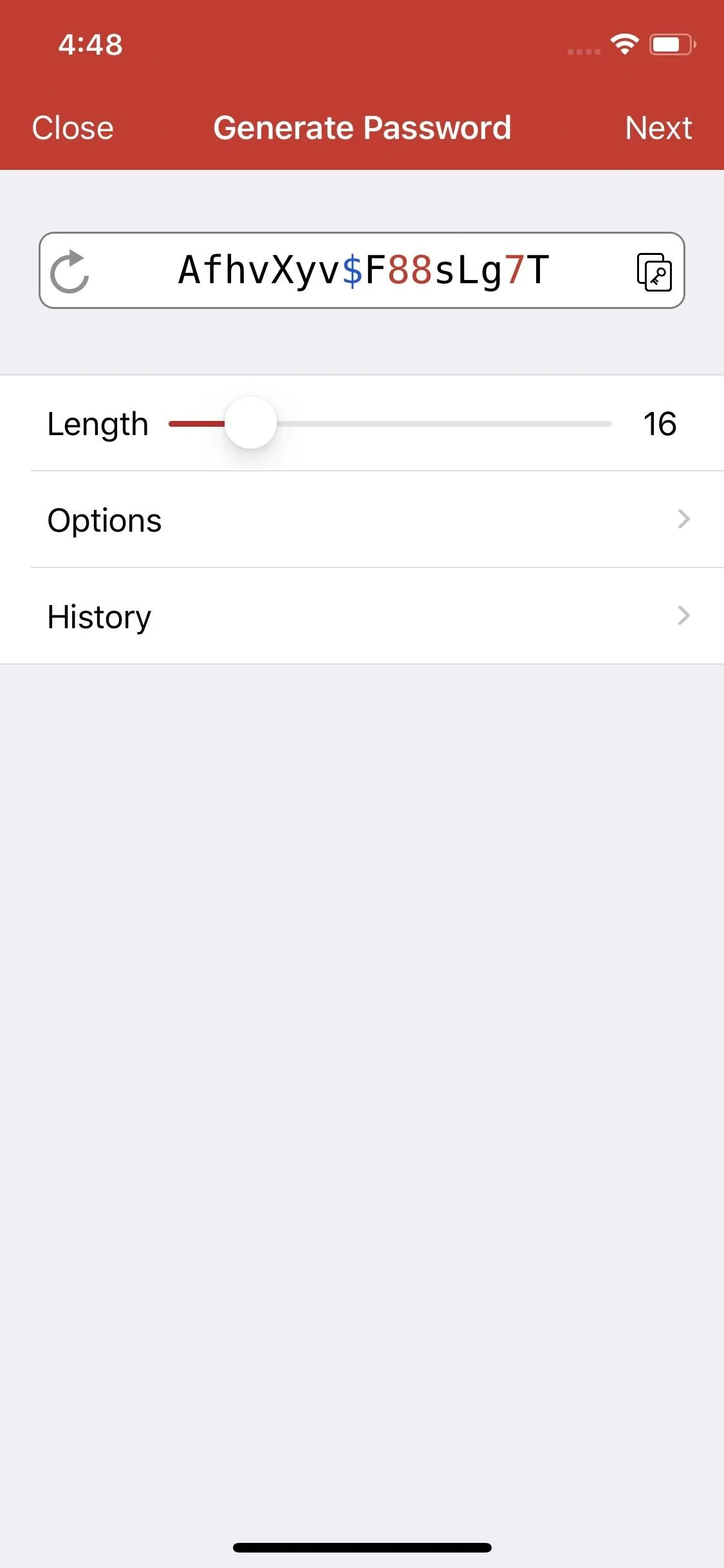
Your first line of defense against any attack is your password. While your user name or email is probably easy for someone else to find, your password is something only you should know. Before a hacker even has to worry about any secondary factors, they need to figure out your password.
The problem is, most people's passwords are terrible. A password manager can help with this by storing all your complex passwords and auto-filling them into your apps when you need them. The passwords are stored in an encrypted database, which itself is protected by one master password. You do need to learn the master password, but since it's only one password it should be easy enough to memorize.


Turn Off Location Tagging
One of the first prompts you will encounter when first opening the camera app is whether you want to enable geotagging. While this feature is excellent for reminiscing, it is also a gateway for hackers or stalkers trying to learn your movements.
Open your Camera app's settings and make sure "geotagging" or "location services" (or similar) is disabled. You'll also want to turn off the location permission for social media apps if you commonly take photos from within the social app instead of your standard Camera app.

Get Rid of Old Accounts
Just because you stop using an account doesn't mean it stops existing. Unattended accounts are a gold mine for hackers since they have nearly an infinite amount of time to break into the account. Once they obtain access to your account, they can set it back to active and wreak havoc.
So delete any account you are not currently using. Use the tools the platform provides to delete the account, and be sure to remove all your data before deletion. Usually, the deleting of social media account has a period before the termination goes into effect, so at least during that time, there is no data to steal.
This article was produced during Gadget Hacks' special coverage on becoming a social media expert on your phone. Check out the whole Social Media series.
Cover image and screenshots by Jon Knight/Gadget Hacks
























Comments
Be the first, drop a comment!